最容易讓你上鉤的十類釣魚郵件

|
作為一名報道網絡安全的記者,危險之一在于黑客們每天都會往我的郵箱里發送釣魚郵件。 如果你不信,可以問問《財富》的母公司時代的安全團隊。 |
One hazard of being a cybersecurity reporter is that attackers send phishing emails to my inbox on a daily basis. If you don't believe me, ask the security team at Time Inc., Fortune's parent company. |
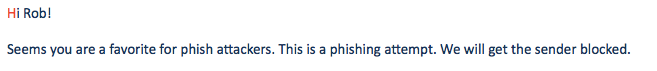
時代的信息安全團隊與我的典型通信內容。2017年6月21日。
?
|
事實上,任何網友都可能成為黑客、間諜和網絡罪犯的目標。你可能認為自己并不是什么特別的人,但是互聯網有趣的一點在于即便你很無趣(當然,考慮到你是《財富》的讀者,你一定不會無趣),黑客仍然可能會攻擊你,可能是為了直接牟利,也可能是把你作為攻擊其他人的墊腳石。 考慮到釣魚的低成本和高成功率,無論是最低級的個人黑客,還是最可怕的由政府支持的計算機破解者,它無疑都是最受青睞的手段之一。近來最著名的釣魚攻擊,也許就是俄羅斯支持的入侵者進入了希拉里·克林頓競選活動的前主席約翰·波德斯達的郵箱,將其內容公布在網上。去年,黑客在美國大選期間入侵了許多國家和地方的選舉數據庫。最近幾周,另一波針對核電廠業務系統的攻擊又得到了曝光。 這些只是近日里關注度最高的釣魚事件。考慮到威脅無處不在,人們最好還是重溫一下攻擊者慣用的誘餌伎倆。在最近的一份研究中,為企業員工提供網絡安全意識培訓的KnowBe4公司總結了釣魚成功率最高的手段。 2017年4月1日至6月30日期間,KnowBe4通過發送欺詐郵件,進行了一項在線自由釣魚測試,看看到底有多少客戶上當。公司給200多萬用戶發送了大約660萬封虛假郵件。以下是十條成功率最高的郵件,一共成功欺騙了22,060人,這些人點擊了信息中的鏈接。(受害者總數要多得多,這里只是被前十名郵件欺騙的人數。) 最成功的釣魚郵件 按主題排序 安全警告 21% 休假/病假政策調整 14% UPS快遞單號:1ZBE312TNY00015011 10% 突發新聞:美聯航乘客死于腦出血——視頻 10% 已嘗試為您投遞包裹 10% 致所有員工:請更新醫療信息 9% 請立刻更改密碼 8% 請立刻驗證密碼 7% 異常登錄行為警告 6% 必須立刻采取行動 6% 以上數據取自欺騙了22,060人的釣魚郵件(2017年第二季度) |
Truth is, anyone online can be a target for hackers, spies, and cybercriminals. You might not think you're that interesting, but the funny thing about networks is that even if you are boring (surely, you mustn't be, given that you're a Fortune reader), hackers may still aim to A) profit from your misfortune, and B) use you as stepping stone to get at someone else. Given its cheap cost and high success rate, phishing has become a favorite scam of everyone from the lowliest crooks to the mightiest state-sponsored computer crackers. Perhaps the most well-known recent example of a phishing attack occurred when likely Moscow-backed intruders pilfered the email inbox of John Podesta, former chairman of Hillary Clinton's presidential campaign, eventually leading to their publication online. Last year hackers infiltrated many state and local election databases in the U.S. during the lead-up to last year's vote. And in recent weeks, another wave of attacks came to light that targeted the business systems of nuclear power plants. These are just some of the recent high profile instances of phishing. Given the pervasiveness of the threat, it's wise for people to brush up on the type of lures that attackers use to bait their victims. In a recent survey, KnowBe4, a firm that provides cybersecurity awareness training for employees, compiled data on the phishing attempts it found most successfully duped people. KnowBe4 measured the number of times clients and participants in its free online free phishing test took the bait of its own trick emails between April 1 and June 30, 2017. During that period, the company sent roughly 6.6 million bogus messages to more than 2 million individuals. Below is data on the top 10 messages; they fooled 22,060 people, each of whom clicked on the links inside the messages. (The number of total victims is much higher, but we're just focusing on those who fell for the top 10 lures.) Most successful phishing emails By subject line Based on phishing emails that tricked 22,060 people (Q2 2017) |
|
從數據中,你可以發現最具有欺騙性的消息。“安全警告”遙遙領先,有超過4,600人上當。其他有關安全的釣魚郵件,例如密碼保護和異常賬戶行為,也有很高的成功率。其他效果突出的伎倆還包括快遞相關的通知,工作相關的信息以及新聞。 KnowBe4表示,平均來看,打開釣魚郵件的用戶里有16%會點擊附帶鏈接。在真正的攻擊情景中,這些都是惡意鏈接,可能會導致登陸信息遭竊,或是系統被強制安裝惡意軟件。而KnowBe4這次測試附帶的鏈接是無害的。 KnowBe4的首席執行官Stu Sjouwerman在接受《財富》采訪時表示,攻擊者往往會選擇公司員工作為目標,因為他們認為“在他們設法進入企業內網時,企業員工最容易讓他們得手”。 他表示:“攻擊媒介里,排名第一的就是電子郵件,所以用戶需要接受培訓,不要點擊郵件中的鏈接,也絕對不要打開未經請求或核實的附件。”(值得一提的是,KnowBe4有44%的攻擊都與LinkedIn消息有關,人們往往會把工作郵箱的地址與LinkedIn關聯。) 以上并不是釣魚郵件的完整清單,只是KnowBe4設計并測試的部分主題。網絡罪犯十分狡猾,他們能想出無數種花樣引你上鉤。 知道人們在哪些情況下最容易受騙,可以幫助你避開那些最危險的騙局。(財富中文網) 譯者:嚴匡正 |
From the data, you can piece together what tends to fool people the most. "Security Alert" leads by a mile, having duped more than 4,600 people. Other lures relating to security had good success too, such as items related to password hygiene and unusual account activity. Other effective tactics involved sending notes purporting to relate to package deliveries, work-related information, and news. On average, KnowBe4 says it finds that 16% of people who open a phishing email click on the links within it. In real attack scenarios, those links or attachments will be malicious, and can lead to a theft of login credentials or the installation of malware onto a device. KnowBe4's links, on the other hand, were benign. Stu Sjouwerman, CEO of KnowBe4, told Fortune that attackers often aim for employees because they consider them "the low-hanging fruit that they can manipulate to get into a network." "The number one attack vector is email, so all users need to be trained to not click on links in emails, and never open an attachment they did not ask for or did not expect without verification," he said. (It's worth noting that 44% of KnowBe4's attacks were related to LinkedIn messages, which people often connect to their work email addresses.) The above is by no means an exhaustive list of phishing lures. These are just some subject lines that KnowBe4 devised and tested. Cybercriminals are a crafty bunch, and there are an infinite number of variations they could try to get the best of you. Knowing what people fall for most can help arm you against the most successful schemes. |











